HTTP headers are important to the way information is transferred on the web. They include essential data regarding web requests and replies, allowing systems to converse well.
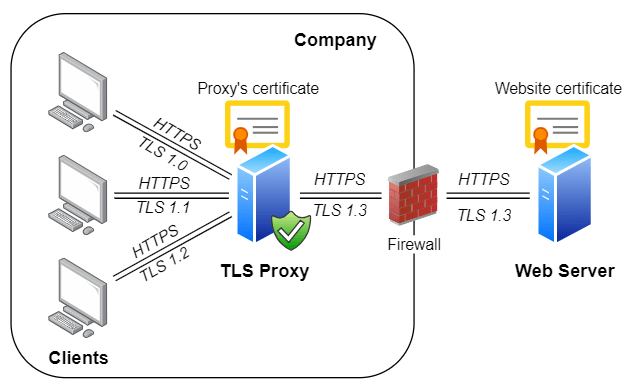
Proxy servers, which perform functions such as request forwarding, traffic balancing, and client anonymity, rely on HTTP headers to function well. But should headers be insecurely or incorrectly configured, they can provide an entry point for security vulnerabilities such as injection attacks.
To ensure proxy servers are securely running, it’s critical to verify HTTP headers. A solid validation process can catch vulnerabilities early and help avoid potential exploits. Tools like the proxy headers test are an easy way to regularly check your header setups, ensuring your system stays secure and reliable.
Understanding HTTP Headers in Proxy Servers
What Are HTTP Headers?
HTTP headers are pieces of information incorporated in request and response packets that harbor metadata about the proposal or client. Headers are utilized to forward information like the type of file being requested, the authentication details, or browser behavior.
The Role of Headers in Proxy Servers
Proxy servers intercept and manipulate HTTP headers to facilitate operations such as:
- Request forwarding (e.g., routing the user’s request to another server).
- Client identity masking is achieved by modifying or removing key header information.
- Traffic management via load balancing techniques.
Common proxy-related HTTP headers:
- X-Forwarded-For (XFF): Shows the original client IP address.
- X-Forwarded-Host (XFH): Reports the original Host header before it arrives at the proxy.
With these capabilities, headers can also become avenues for vulnerabilities if not configured securely.
Risks Associated with Improper Header Configurations
Headers that are inadequately managed or left unchecked open the door to significant risks:
- Header Injection and Spoofing:
Malicious headers may be injected by attackers in transit, allowing requests to be smuggled, cache poisoned, or sessions hijacked.
- Web Cache Poisoning:
An adversary can manipulate header inputs to craft harmful payloads, tricking web applications into caching harmful responses.
- Cross-Site Scripting (XSS) Vulnerabilities:
Weakly sanitized headers may serve as the attackers’ entry point for running scripts in victims’ browsers.
Organizations such as OWASP emphasize the significance of secure header settings in configurations. These are assisted by the OWASP Secure Headers Project, which gives best practices on how best to secure HTTP headers to provide strong defenses against these attack vectors.
Implementing a Header Validation Framework
To address these security challenges, implementing a header validation framework is essential. Here are the core steps:
1. Whitelist Trusted Headers
Only allow specific, pre-validated headers in HTTP requests. Reject any headers not explicitly approved to prevent unexpected behavior.
2. Sanitize Incoming Values
Sanitize client-provided inputs to remove any potentially malicious data. For example:
- Strip out characters or sequences that could lead to injection attacks.
- Validate values against defined expected formats.
3. Enforce Header Policies Automatically
Use automated monitoring and enforcement tools to test and implement header security policies consistently. This will help organizations proactively identify misconfigurations or policy loopholes.
4. Leverage Logging and Alerts
Set up detailed logging for header activities within your proxy server. Combine this with real-time alerts to identify suspicious patterns that could indicate compromise.
Utilizing Proxy Headers Test Tools
Regular testing is critical for identifying configuration issues. A proxy headers test can automate this process:
- Detect anomalies or missing headers. It confirms all required headers, such as X-Forwarded-For or X-Forwarded-Host, are in position and appropriately configured.
- Uncover vulnerabilities early. The tool checks for deviations in your header security configurations.
- Ensure compliance. Proxy headers tests ensure that your setup adheres to industry best practices.
Testing not only strengthens your header validation framework but also provides actionable insights to maintain and update configurations.
Best Practices for Secure Header Management
To optimize security:
Regularly Update Proxy Software:
Keep your proxy server software up-to-date to address known vulnerabilities.
Apply Strict Validation Rules:
Implement detailed validation for both incoming and outgoing headers.
Conduct Routine Security Audits:
Use penetration testing to uncover weaknesses in header configurations.
Stay Updated on Emerging Threats:
Monitor threat intelligence and adjust configurations to tackle evolving risks.
Use a Content Security Policy (CSP):
A well-defined CSP, along with secure headers like X-Content-Type-Options and Referrer-Policy, enhances web application security.
For more on attacks like cache poisoning or host header attacks, consult PortSwigger’s guide to understand and mitigate risks from faulty configurations.
Conclusion
HTTP headers are critical for web operations, but mismanagement can have serious consequences. Adopting validation frameworks, advanced testing tools, and best practices helps organizations protect proxy configurations against threats. Proper HTTP header management ensures security, stability, and user trust in your digital environment.